Today we’re ecstatic to publish our first demo showing a homemade BusKill Cable (in the prototype 3D-printed case) triggering a lockscreen.
| Watch the 3D-Printed USB Dead Man Switch (Prototype Demo) for more info youtube.com/v/vFTQatw94VU |
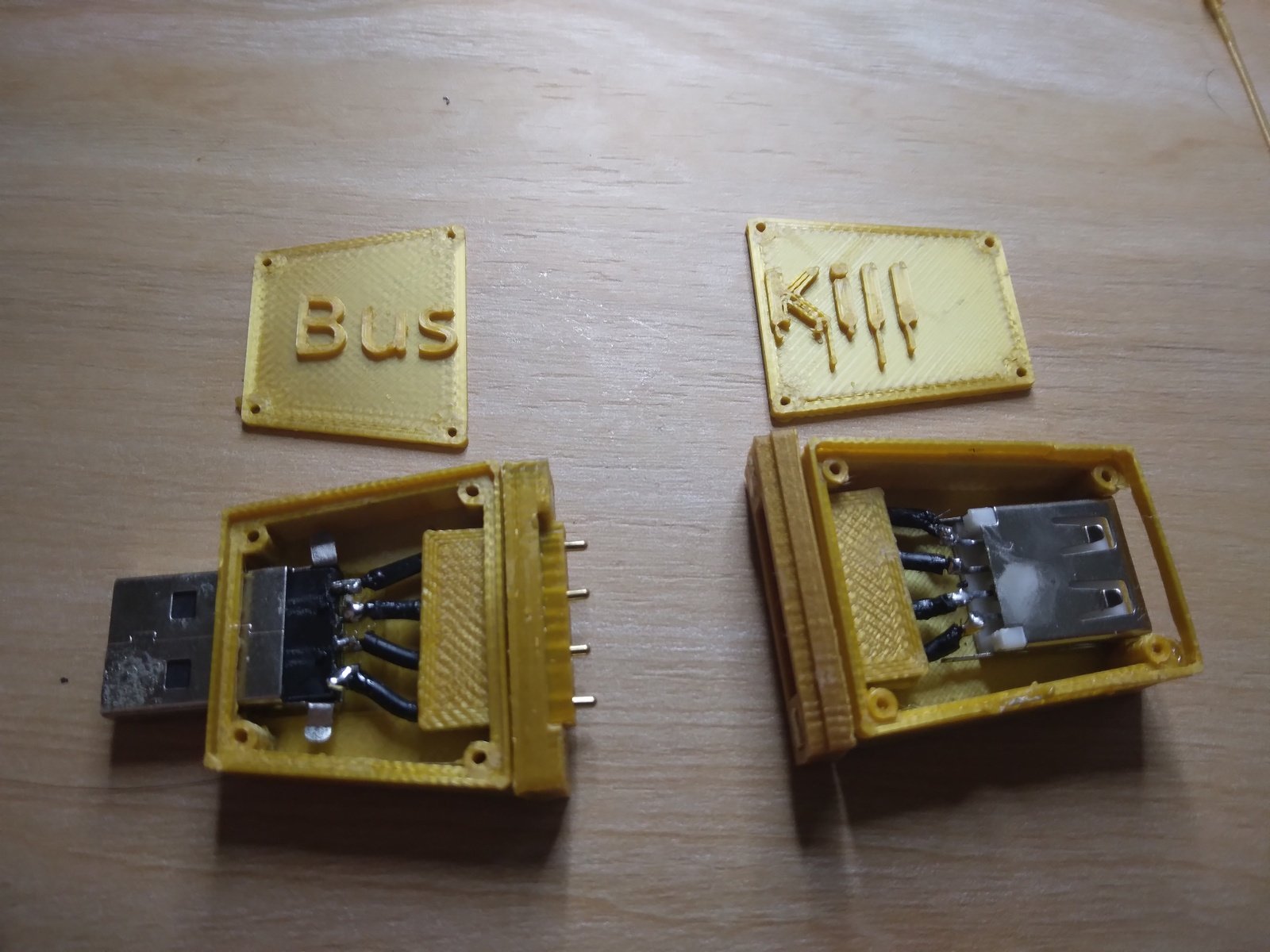
In our last update, I showed a video demo where I successfully triggered a lockscreen using a BusKill prototype without the 3D-printed body for the case and N35 disc magnets. I realized that the N35 disc magnets were not strong enough. In this update, I show a demo with the prototype built inside a 3D-printed case and with (stronger) N42 and N52 cube magnets.
What is BusKill?
BusKill is a laptop kill-cord. It’s a USB cable with a magnetic breakaway that you attach to your body and connect to your computer.
 |
|---|
| Watch the BusKill Explainer Video for more info youtube.com/v/qPwyoD_cQR4 |
If the connection between you to your computer is severed, then your device will lock, shutdown, or shred its encryption keys – thus keeping your encrypted data safe from thieves that steal your device.
Why?
While we do what we can to allow at-risk folks to purchase BusKill cables anonymously, there is always the risk of interdiction.
We don’t consider hologram stickers or tamper-evident tape/crisps/glitter to be sufficient solutions to supply-chain security. Rather, the solution to these attacks is to build open-source, easily inspectable hardware whose integrity can be validated without damaging the device and without sophisticated technology.
Actually, the best way to confirm the integrity of your hardware is to build it yourself. Fortunately, BusKill doesn’t have any circuit boards, microcontrollers, or silicon; it’s trivial to print your own BusKill cable – which is essentially a USB extension cable with a magnetic breakaway in the middle
Mitigating interdiction via 3D printing is one of many reasons that Melanie Allen has been diligently working on prototyping a 3D-printable BusKill cable this year. In this article, we hope to showcase her progress and provide you with some OpenSCAD and .stl files you can use to build your own version of the prototype, if you want to help us test and improve the design.
Print BusKill
If you’d like to reproduce our experiment and print your own BusKill cable prototype, you can download the stl files and read our instructions here:
Iterate with us!
If you have access to a 3D Printer, you have basic EE experience, or you’d like to help us test our 3D printable BusKill prototype, please let us know. The whole is greater than the sum of its parts, and we’re eager to finish-off this 3D printable BusKill prototype to help make this security-critical tool accessible to more people world-wide!
Smaller versions of this have decent real-world applications. Good prototype, but shrink it to USB size now and you’ve got phone security. Will be interesting to see how this develops.
Do you have any tips on soldering solutions that would allow us to decrease the size?
Unfortunately, it’s already extremely difficult to solder the pins and glue the magnets at the current size. I think it’s important to lower the barrier of entry for people with just basic soldering and printing tools to be able to make this. But if you have any recommendations to shrink the size without also making it impossible for most hackers to build themselves, we’re all ears :)
fwiw, we do have an injection molded version that’s much smaller, but it requires very expensive equipment to make (which is one reason we’re developing this 3D-printable version as an alternative)
Here is an alternative Piped link(s):
3D-Printed USB Dead Man Switch (Prototype Demo)
Piped is a privacy-respecting open-source alternative frontend to YouTube.
I’m open-source; check me out at GitHub.
Ross Ulbricht wishes he had one of these.
To prevent Ulbricht from encrypting or deleting files on the laptop he was using to run the site as he was arrested, two agents pretended to be quarreling lovers. When they had sufficiently distracted him,[34] according to Joshuah Bearman of Wired, they quickly moved in to arrest him while a third agent grabbed the laptop and handed it to agent Thomas Kiernan.[35] Kiernan then inserted a flash drive into one of the laptop’s USB ports, with software that copied key files.[34]
Wow you weren’t kidding.